Today, where screens have become the dominant feature of our lives and our lives are dominated by screens, the appeal of tangible, printed materials hasn't diminished. It doesn't matter if it's for educational reasons for creative projects, simply adding an extra personal touch to your home, printables for free are now an essential resource. This article will take a dive deeper into "Collision Attack Example," exploring the benefits of them, where to get them, as well as how they can add value to various aspects of your lives.
Get Latest Collision Attack Example Below

Collision Attack Example
Collision Attack Example -
A collision attack is the ability to find two inputs that produce the same result but that result is not known ahead of time In a typical case e g the attack on MD5 only a relatively
Many applications of cryptographic hash functions do not rely on collision resistance thus collision attacks do not affect their security For example HMACs are not vulnerable For the attack to be useful the attacker must be in control of the input to the hash function Because digital signature algorithms cannot sign a large amount of data efficiently most implementations use a hash function to reduce compress the amount of data that needs to b
Collision Attack Example offer a wide array of printable resources available online for download at no cost. These materials come in a variety of kinds, including worksheets templates, coloring pages and more. The appeal of printables for free is their flexibility and accessibility.
More of Collision Attack Example
Seed Labs MD5 Collision Attack YouTube

Seed Labs MD5 Collision Attack YouTube
There are different ways to detect hash collisions in files Two files if you have two or more files with different contents and the same hash just diff them However if you only have a single file it can be difficult to tell if
A successful SHA 1 collision attack by Google and CWI researchers means the cryptographic hash function is no longer secure Find out how the attack works
Collision Attack Example have garnered immense recognition for a variety of compelling motives:
-
Cost-Efficiency: They eliminate the requirement to purchase physical copies or expensive software.
-
Personalization There is the possibility of tailoring printables to fit your particular needs for invitations, whether that's creating them and schedules, or even decorating your home.
-
Educational Value Free educational printables cater to learners from all ages, making them an essential tool for parents and teachers.
-
Easy to use: Instant access to a variety of designs and templates, which saves time as well as effort.
Where to Find more Collision Attack Example
SHA 1 Collision Attack Techfeedthai

SHA 1 Collision Attack Techfeedthai
A collision attack is a cryptographic attack that aims to find two distinct inputs that hash to the same output In other words the attacker seeks to identify two different messages
A collision attack is a type of cyber attack that seeks to exploit vulnerabilities in a system by causing two different inputs to produce the same output This can be done for example by causing two different
Now that we've ignited your curiosity about Collision Attack Example Let's look into where you can discover these hidden treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy provide a variety of Collision Attack Example for various purposes.
- Explore categories such as decorating your home, education, craft, and organization.
2. Educational Platforms
- Forums and educational websites often provide worksheets that can be printed for free for flashcards, lessons, and worksheets. tools.
- Ideal for parents, teachers, and students seeking supplemental resources.
3. Creative Blogs
- Many bloggers post their original designs and templates, which are free.
- The blogs covered cover a wide array of topics, ranging all the way from DIY projects to party planning.
Maximizing Collision Attack Example
Here are some innovative ways of making the most use of Collision Attack Example:
1. Home Decor
- Print and frame stunning artwork, quotes or other seasonal decorations to fill your living spaces.
2. Education
- Use these printable worksheets free of charge to reinforce learning at home (or in the learning environment).
3. Event Planning
- Invitations, banners and decorations for special events like weddings or birthdays.
4. Organization
- Get organized with printable calendars along with lists of tasks, and meal planners.
Conclusion
Collision Attack Example are an abundance of practical and innovative resources that meet a variety of needs and preferences. Their availability and versatility make these printables a useful addition to each day life. Explore the vast array of Collision Attack Example now and unlock new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables for free really free?
- Yes you can! You can download and print these items for free.
-
Can I utilize free printables for commercial uses?
- It's determined by the specific terms of use. Always check the creator's guidelines prior to using the printables in commercial projects.
-
Do you have any copyright concerns with Collision Attack Example?
- Certain printables might have limitations in use. Always read the terms and conditions set forth by the designer.
-
How do I print Collision Attack Example?
- Print them at home with your printer or visit the local print shop for top quality prints.
-
What program do I need to run printables that are free?
- Many printables are offered in the PDF format, and can be opened using free software like Adobe Reader.
collision Attack
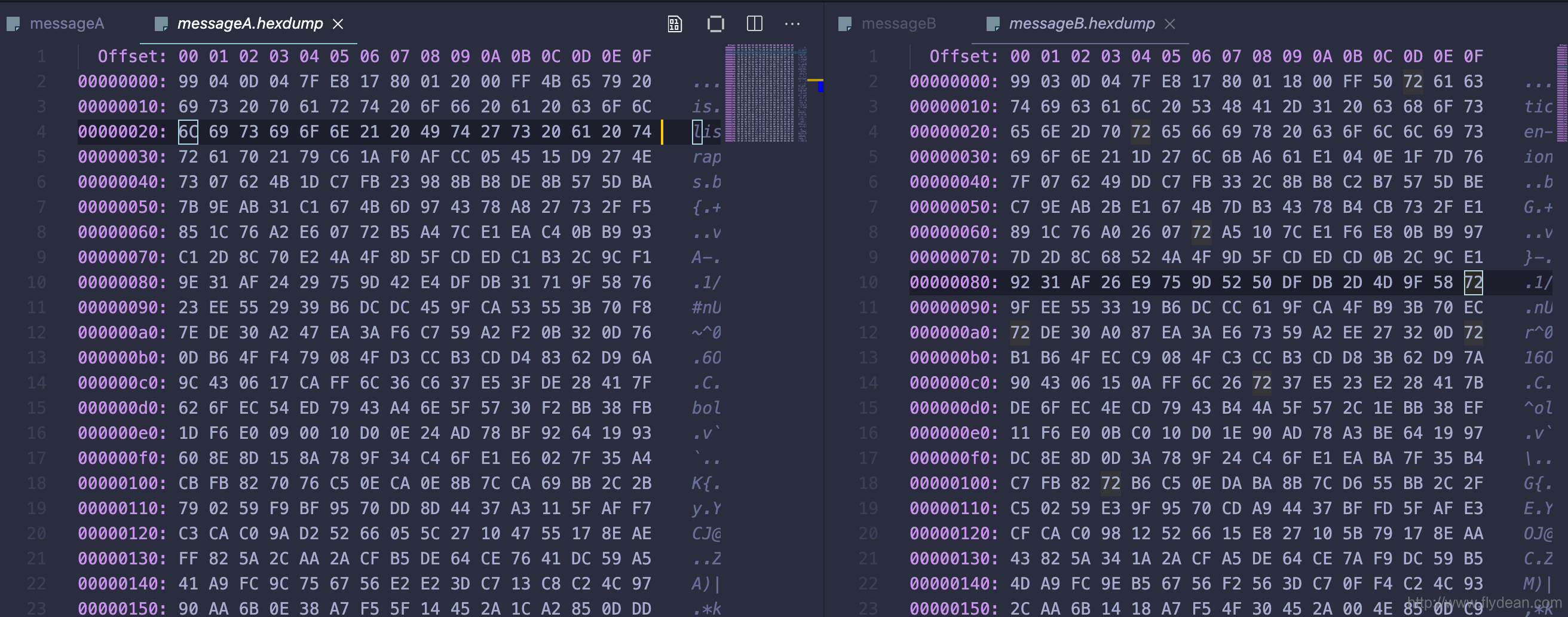
2 Outline Of The Functional Collision Attack Download Scientific Diagram

Check more sample of Collision Attack Example below
MD5 Collision Attack Lab Task1 And Task 2 YouTube

What Is A Collision Attack

MD5 Generator Online MD5 Calculator

Hash Collision Attack Privacy Canada

SEED lab MD5 Collision Attack Lab
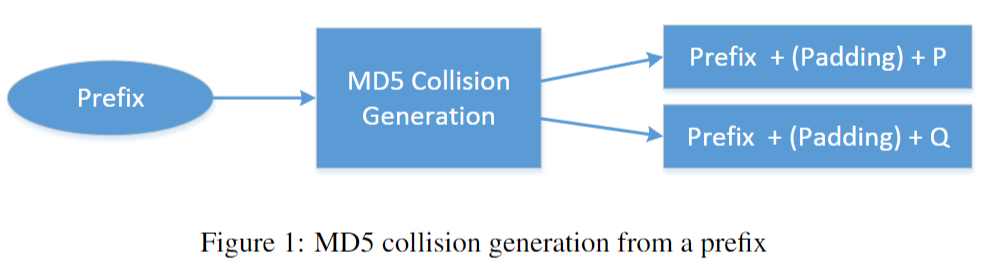
What Is A Collision Attack


https://en.wikipedia.org/wiki/Collision_attack
Many applications of cryptographic hash functions do not rely on collision resistance thus collision attacks do not affect their security For example HMACs are not vulnerable For the attack to be useful the attacker must be in control of the input to the hash function Because digital signature algorithms cannot sign a large amount of data efficiently most implementations use a hash function to reduce compress the amount of data that needs to b

https://www.comparitech.com/blog/infor…
What is a collision attack A collision attack is simply when an attacker finds one of these collisions and uses it to undermine the security that the hash was assumed to provide Collision attack
Many applications of cryptographic hash functions do not rely on collision resistance thus collision attacks do not affect their security For example HMACs are not vulnerable For the attack to be useful the attacker must be in control of the input to the hash function Because digital signature algorithms cannot sign a large amount of data efficiently most implementations use a hash function to reduce compress the amount of data that needs to b
What is a collision attack A collision attack is simply when an attacker finds one of these collisions and uses it to undermine the security that the hash was assumed to provide Collision attack

Hash Collision Attack Privacy Canada

What Is A Collision Attack

SEED lab MD5 Collision Attack Lab

What Is A Collision Attack

CISSP Collision Attack YouTube

SHA 1 Shattered Collision Attack Stock Vector Image Art Alamy

SHA 1 Shattered Collision Attack Stock Vector Image Art Alamy

First Practical SHA 1 Collision Attack Arrives Threatpost The First Stop For Security News